SOCs and incident response teams engage with all forms of toxic content and encounter bad actors every day. Whether validating potentially malicious links, investigating phishing campaigns, assessing takedowns for brand misuse or looking into signals from cybersecurity intelligence solutions, analysts expose themselves and their organizations to major risks.
Silo for Research isolates web browsing to neutralize toxic content and provides analysts with a purpose-built solution to manage their digital fingerprint and conduct investigations efficiently.

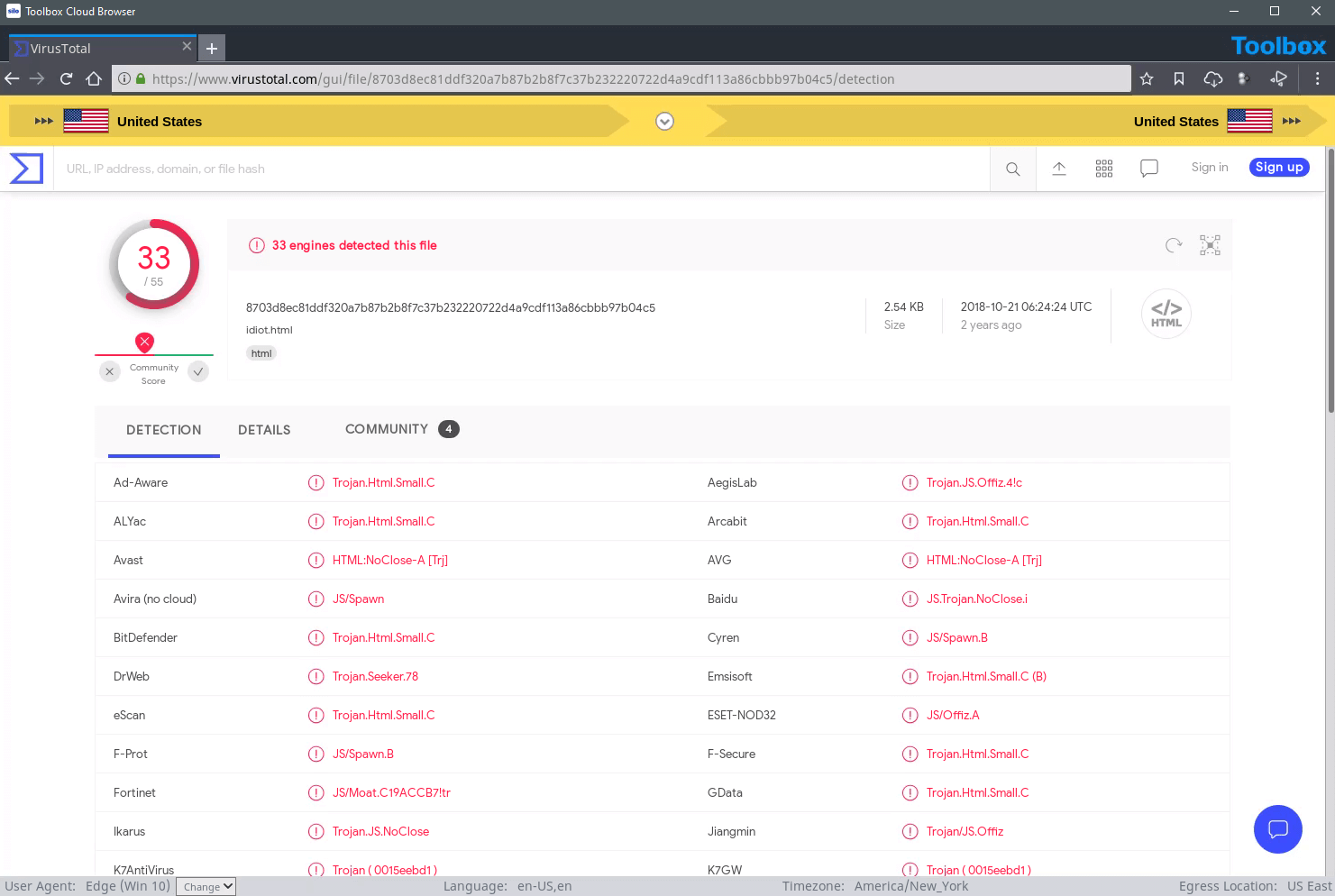
Silo for Research executes 100% of web code on a secure, remote host in the cloud, and collected assets can be stored in an encrypted off-site storage repository. No web-native data reaches the endpoint — ever — whether conducting security intelligence research on the surface, deep or dark web.
For analysts requiring dark web research, Silo for Research: Dark Web provides point-and-click access, without the need to install and manage additional software.
Silo for Research never reveals analysts’ identity, affiliation or intent — no matter the computer or network used. Show a local IP that never refers back to your organization and a user agent configured to fit the scenario (device type, OS, browser, etc.). Appear as an in-region visitor to prevent websites from showing different information. With Silo for Research, security intelligence analysts have the tools to spoof location, platform attributes, language and more.
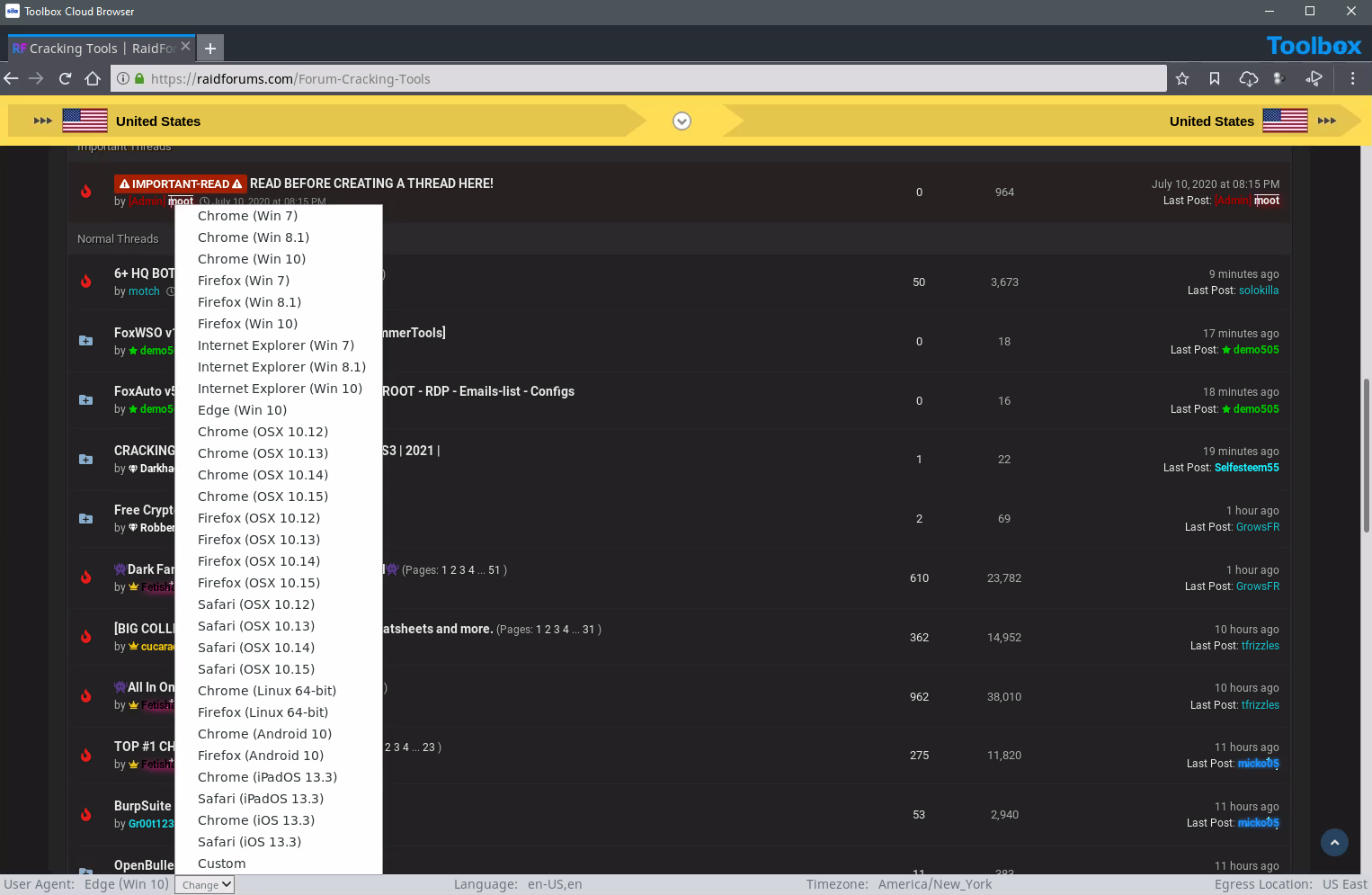
Silo for Research is purpose-built for sensitive online cybersecurity intelligence investigations, giving analysts a single-pane-of-glass workspace and a suite of integrated tools to improve efficiency while maintaining tradecraft. Translate out of band, automate multi-search and use built-in dev tools to analyze packets and review source code and web linkages. Streamline collection from screen capture to annotation, asset and URL timestamping, and even automated, scheduled collections.
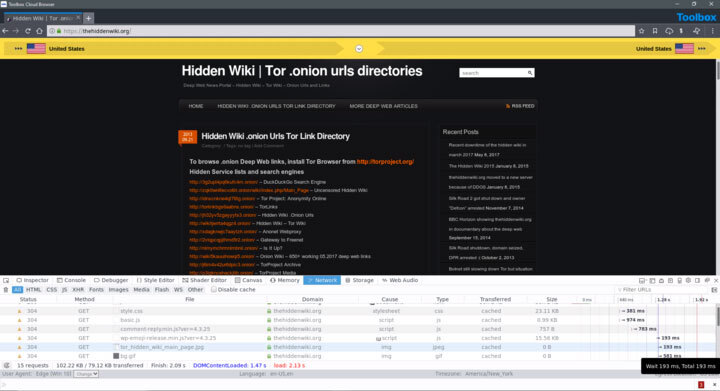




With Silo for Research's managed attribution functionality, you can completely customize how you appear to sites and people that you interact with online by manipulating a variety of your device details including language, time zone and keyboard settings, as well as the browser, OS and other elements. Using Authentic8's global egress network, you can adjust your physical location to appear to be coming from any of dozens of points around the world, showing a local IP address that never refers back to you or your organization.
Yes, dark web access is seamlessly integrated within Silo for Research and its suite of analyst tools. You do not need a separate, standalone dark web browser. This integration provides investigators with full isolation from dark web cyberthreats (e.g., malware-laden sites, forums, marketplaces) and anonymity from counter-surveillance efforts utilized by malicious actors.
Yes, Silo for Research integrates with Authentic8 Secure Storage, an encrypted, audited and cloud-based storage repository for users and groups. Investigators may be required to capture and collect content as part of their process. And to maintain efficacy of potential evidence, a proper chain of control and evidentiary requirements must be met.
Collected data needs to be logged, attributed to an analyst and checked for validity. Chain of custody protections are critical to proper collection. When using Silo for Research collection tools — whether manual or automated — all aspects of the process are logged and available for post-facto review.
Yes, Silo for Research is a FedRAMP-authorized service. It has been assessed and approved as a cloud service offering (CSO) that meets the stringent security requirements to process, store and transmit federal government data.