Considering where cyberthreat intelligence teams should reside in the organizational structure can make a major difference in the intelligence they can produce and how it’s used.
Many organizations are starting their journey into either building a cyberthreat intelligence team (CTI) or augmenting their current cybersecurity teams into a mixed CTI team. This begs the question as to where in the organization should the CTI team be placed and who do they report to in the organization?
Existing organizational structures may not be the best fit for the current function of CTI. In order for CTI teams to focus on building intelligence on threats against the organization, they need to be kept out of response based on that intelligence. Their work informs the response — as carried out by the security operations center (SOC) or similar team — but should not be distracted by it. Similarly, CTI teams should not be subject to risk frameworks — as defined by risk management or other teams. This can skew the reports CTI teams produce with organizationally biased intelligence.
For the best results from a CTI team, let’s look at the composition of roles, existing organizational structures and the potential for new structures.
Building a CTI team
Before we attempt to answer that question, we need to talk about the best way to build a CTI team. Do you start from scratch, hiring people with experience in any form of intelligence analysis, who can distill complex information for consumption by a general audience? Or do you create a team from internal personnel who have experience in cybersecurity, like members from the SOC?
Let’s begin by looking at probably the simplest and most cost-effective way by creating a CTI team: from within. There are many advantages to establishing a CTI team with existing personnel and SOC members as they have intimate knowledge of the existing security environment of the organization. This means that when it comes to identifying threats to an organization they have a better grasp on current security architecture and controls that have been put in place to protect the organization.
The second way to build a CTI team is to hire people from outside of the organization. This is a difficult thing to do from a financial standpoint due to the high cost of experienced cybersecurity professionals or intelligence professionals that an organization would need for this new CTI team. These individuals will take a significant time to get up to speed on the specific security environment and controls that have been implemented along with understanding the specific threats to the organization they will be joining. There may be other things that cause this new team to not reach their full potential within the first year whether it is financial constraints or not being able to get management on their side for what is needed for a CTI team.
My recipe for the best CTI team makeup
Regardless of whether you hire from inside or outside of the organization, it’s important to consider the ideal composition of the team.
Cyberthreat intelligence manager
Needs to have a background in intelligence along with strong cybersecurity capability for the creation of documentation necessary for the creation of the CTI team.
Senior cyberthreat intelligence analyst/intelligence chief
An experienced intelligence professional who is able to review intelligence reports for errors, assist in analysis and training of junior analysts but is not in a managerial position. Must be able to brief senior management and C-Suite personnel.
Junior analysts
The following is a preferred breakdown of a small team (three to five personnel) that could then be built into a larger intelligence organization
- Vulnerability analyst: Focuses on providing analysis and potential threat reporting based on vulnerabilities that are identified either as threats by the vulnerability management team or from open-source reporting. Will work hand in hand with the vulnerability management team to provide the best analysis when it comes to newly released vulnerabilities and their potential impact on the organization.
- Fraud analyst: Focuses on the identification and remediation of fraudulent activities that impact the organization. Has a clear understanding of how fraudsters work and how to identify their activities on a network. Works hand in hand with the fraud team at the organization to provide better alerts and early detection of fraudulent activities.
- Network/computer security analyst: Focuses on network/computer security and is potentially someone who has worked in a cybersecurity operations center (CSOC) but is also someone who has in-depth knowledge of the organization's network security controls. Additionally, this individual has an in-depth understanding of how computers work so they are able to explain how something may impact the organization at the bit/byte level.
- Threat hunter/insider threat analyst: Focuses on protecting the organization from internal threats along with searching the organization’s network for breaches that were missed or not identified by other security controls. Should have complete understanding of the organization’s network and where threats may likely be hiding on top of understanding where insider threats originate.
- All-source intelligence analyst/report writer: Focuses on taking all the information provided by the above analysts and building reports, along with being able to conduct any research that is necessary to assist the other analysts. While it’s not 100% necessary for this individual to have a background in cybersecurity, having the ability to learn and understand the other members' roles is crucial. If the analyst has a background in cybersecurity, they can assist the CTI manager and the senior intelligence analyst in the creation of necessary documentation and review of security controls implemented by the organization.
This is a rough composition of a well-rounded team that would be able to provide threat assessments and intelligence to almost any organization. Additionally, if the organization becomes large enough you could then take the roles and create teams with a manager and two or three analysts underneath those teams, further expanding the organization’s capabilities.
Benefits of this composition
“One fundamental issue I have seen when it comes to CTI teams is that they get turned into providing risk assessments based on intelligence and not an intelligence assessment based on threats to the organization.”
-(me) Adam Huenke
One of the first benefits of this type of team composition is that it includes the personnel with skills needed to cover the majority of the issues that organizations face on a daily basis. With a collection of various subject matter experts, your CTI team can focus on the most valuable disciplines for providing intelligence across the organization, to include management, C-Suite and the board of directors.
Another benefit is that the analysts are trained and enabled to focus on their assigned tasks and develop expertise relevant to their organization’s threat environment. This allows for rapid and accurate dissemination of intelligence to be provided to the people that need it.
The last benefit is the fact that these sections can work with their respective counterparts within the organization to gain a better understanding of that function so that the CTI team can provide the best intelligence possible, allowing the organization to make informed decisions.
Overall, this composition allows for the best intelligence to be provided to all levels of the organization. Notice here I have not mentioned anything about risk, risk reduction, risk management, or risk ratings. This is because one fundamental issue I have seen when it comes to CTI teams is that they get turned into providing risk assessments based on intelligence and not an intelligence assessment based on threats to the organization. At the end of the day, CTI teams provide intelligence assessments and recommendations but are not the decision-makers on what happens. This is the only way to provide a true intelligence function to an organization.
Where current CTI teams reside — and why that’s a problem
CTI teams may reside in different departments at an organization, depending upon the business sector or size of the organization.
There are some CTI teams that are members of the SOC or CSOC, as these are the front line of defense for the organization. Teams that reside at this level mainly help with incident response and, due to the reactionary nature of this arrangement, provide little to no intelligence to the organization as a whole. Teams at this level can be limited in their ability to build and disseminate full intelligence reports that provide value to an organization.
CTI teams may also sit within the risk management space of an organization. Sometimes organizations even start a whole new section called “cyber risk management” separate from the traditional risk management team to focus on cyber risk. A team in this position will likely end up focusing on building intelligence to support the risk framework that has been adopted by the organization. Pressure to comply with the frameworks may cause CTI analysts to downplay certain threats and oversell other threats based on an arbitrary risk score defined by the organization.
Many organizations today tend to equate a threat to a risk, which is a false equivalence. Let’s look at the Department of Homeland Security’s definitions of these terms:
- “Threat: Natural or man-made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment and/or property.”
- “Risk: potential for an unwanted outcome resulting from an incident, event, or occurrence, as determined by its likelihood and the associated consequences.”
In other words, a threat is the potential for harm whereas a risk takes into account other factors based on not only a threat but also the controls in place to stop that threat.
Sometimes all-source analysts or cyberthreat analysts do not have the expertise or experience to provide an accurate risk assessment to an organization.
Overall, the risk to an organization is calculated as the combination of threats and vulnerabilities which means that in some situations, threats may exist but without any vulnerabilities, there is a result of little to no risk; and conversely, you could have vulnerabilities with no threats with the same result of little to no risk. This is why CTI teams need to focus on providing intelligence on the threats against the organization and not the risk against the organization.
Where CTI teams should reside and who they should answer to
When we start looking at where CTI teams should reside, there are many people who feel they are perfect right where they are. But there are some, including me, that feel there is a better position for the CTI team.
A great article by A.J. Nash, vice president of intelligence at ZeroFOX, outlines a new role in organizations that CTI teams would answer to: the chief intelligence officer (CINO). This person would be at the C-suite level, answer directly to the CEO and work hand in hand with the CISO (see figure 1). The role would also answer to the board of directors or be on the board itself. Based on this new role, the CTI team would fall under the leadership of the CINO in the rough composition I laid out above and would no longer be a CTI team but a threat intelligence (TI) organization.
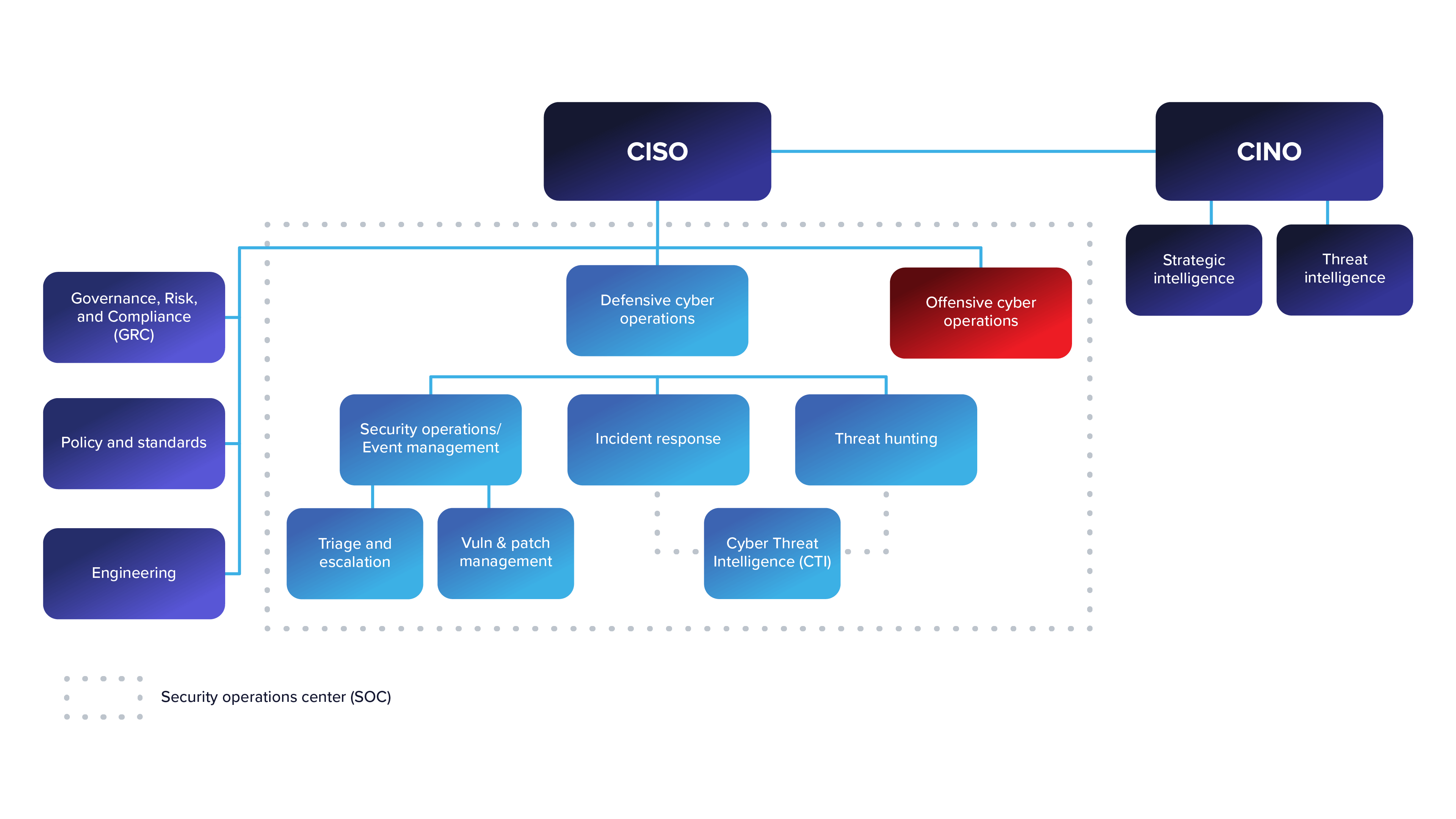
Figure 1: Example of CINO-led threat intelligence team (Source: Nash, US Cybersecurity Magazine)
Having the CTI team outside of the normal organizational structure — not under the CISO or CIO — allows for that team to provide real, actionable information and intelligence that is not driven by operations (see figures 2 and 3). Additionally, it allows for the expansion of the mandates that have been given to the CTI team and would be an easy adjustment, according to Nash; I tend to agree with this proposal. Overall, this would change the team to a TI entity not only focused on cyberthreats but all threats to an organization.
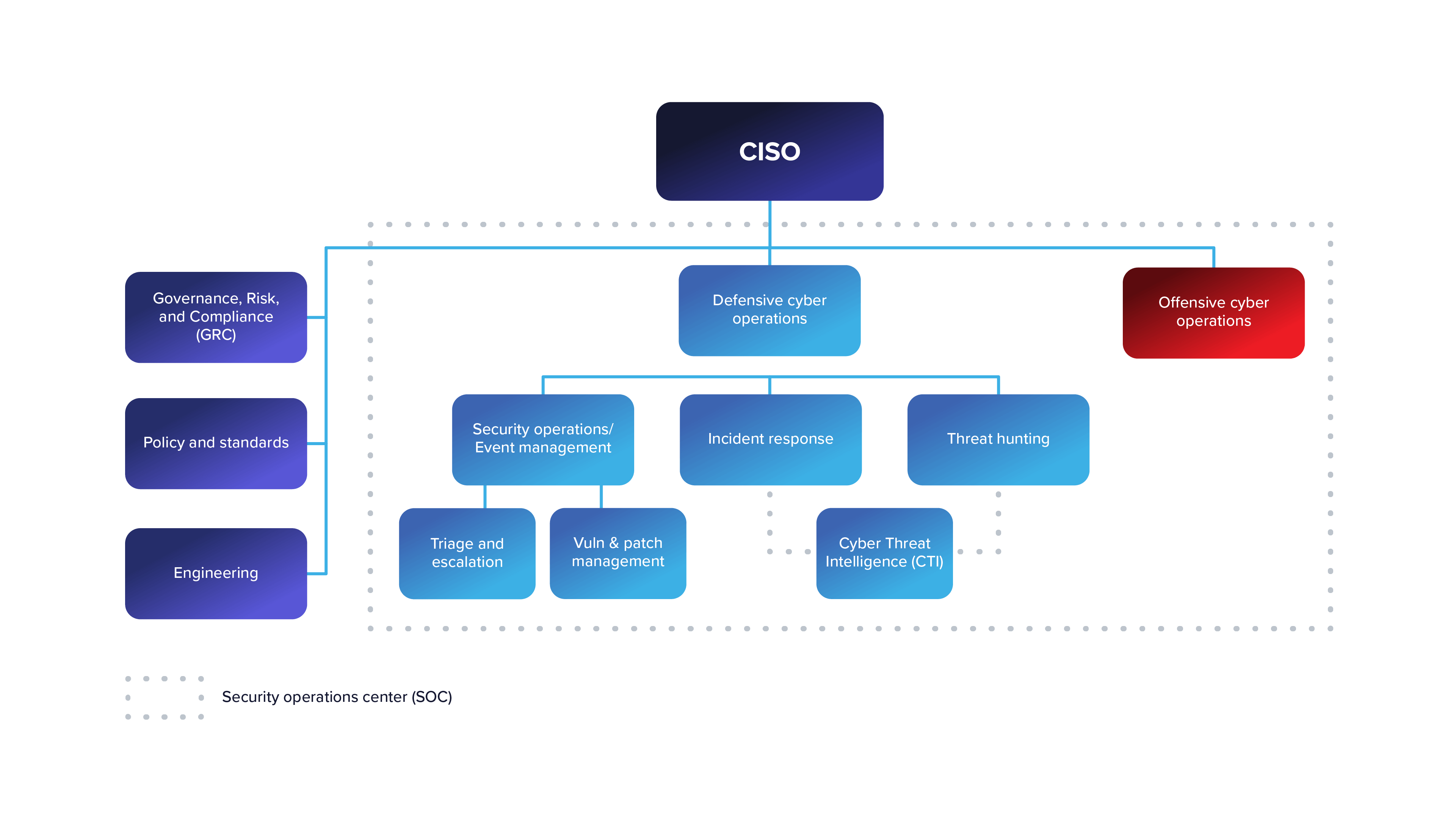
Figure 2: Example of CISO-lead cyberthreat intelligence team (Source: Nash, US Cybersecurity Magazine)
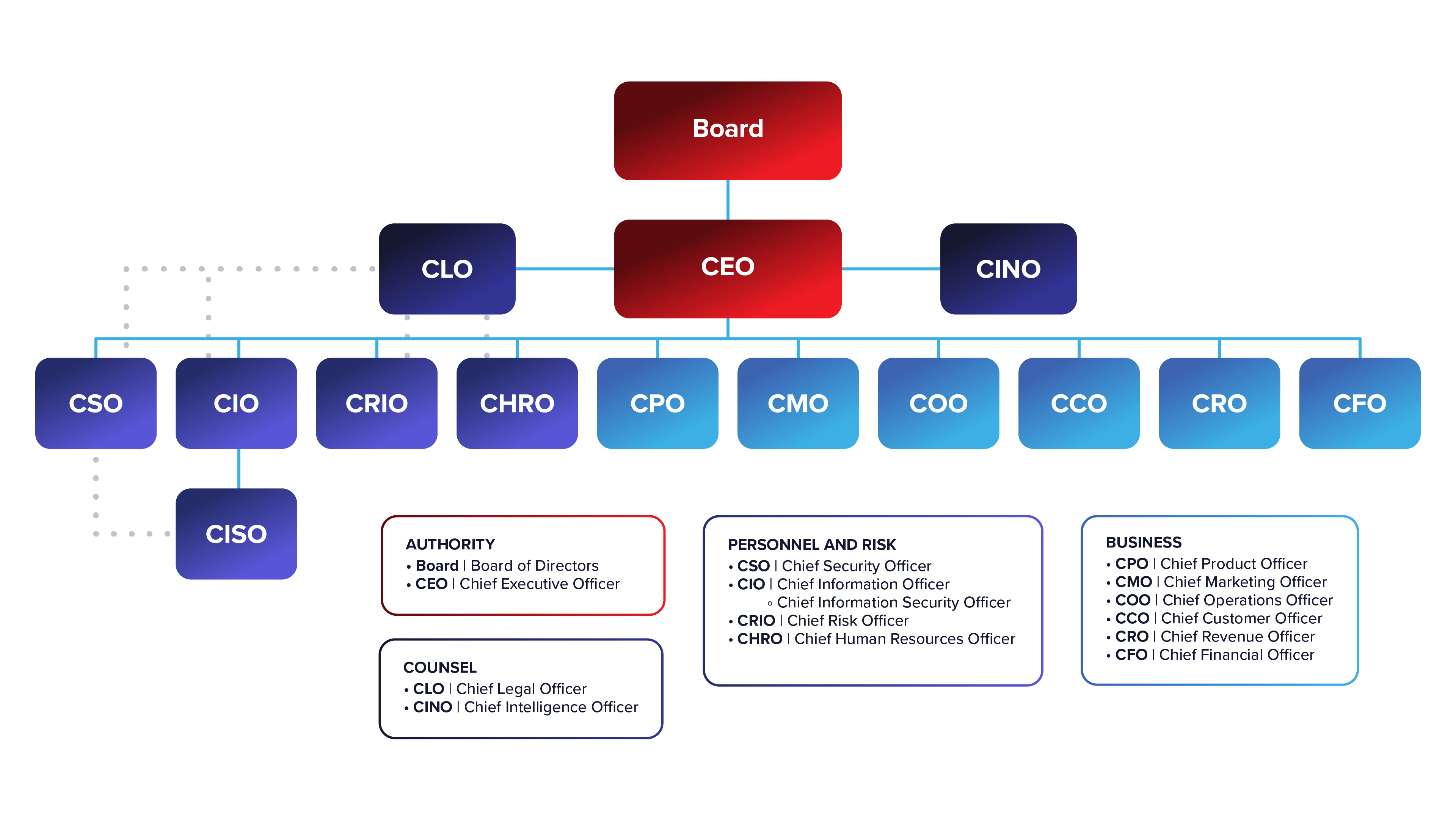
Figure 3: Example of CINO in broader organizational structure (Source: Nash, US Cybersecurity Magazine)
Moving the CTI team either directly under the CISO or a TI team under this new CINO is the best way for members to provide information/intelligence without the pressure to recommend a specific decision based on other factors outside of their control.
To learn how Authentic8 can help CTI, SOC and cybersecurity teams better investigate threats, visit our webpage.
Tags SOC Threat intelligence

