Agencies of all types need to maximize the intelligence gleaned from publicly available information across the surface, deep and dark web. To do so investigators must be able to access the internet locally from within a given region and manage their digital fingerprint to blend in with other traffic and users.
Whether monitoring assets, investigating illicit trafficking or building case files on specific targets, analysts across federal, local and private investigation agencies rely on Silo for Research — the only FedRAMP-authorized research platform.

Whether tracking events across sites or engaging with external parties online, Silo for Research gives you the tools to spoof your location, platform attributes, language and more — even if using your home computer. Execute searches from dozens of geographies, showing a local IP that never refers back to your organization and a user agent configured to fit the scenario. You can even launch multiple, unique environments in a single viewing space to easily move between OSINT investigations.
Silo for Research provides point-and-click access to surface, deep and dark web content from a single, integrated environment. Researchers can seamlessly switch context, as required by their investigations. Dark web access is integrated into the platform eliminating the need to install and manage additional software. Along with comprehensive audit oversight, the platform's isolation and anonymity extend to the dark web, protecting analysts from counter-intelligence and malware threats.
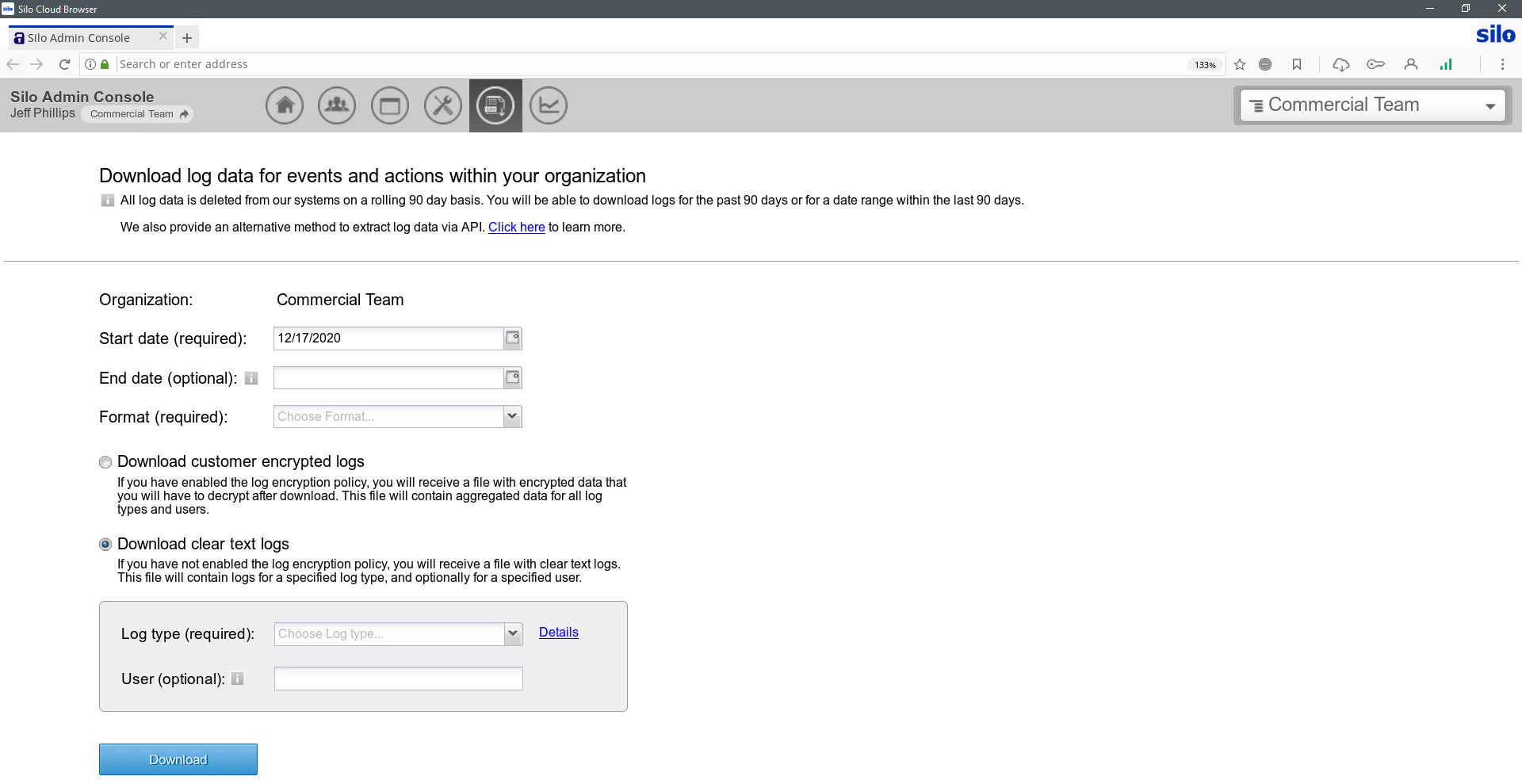
Some OSINT investigations lead to more formal reviews by internal teams, regulators or the courts. Presenting evidentiary logs and case materials starts with centralized processes and clear custodial records. Silo for Research provides a single framework for tracking collections and monitoring investigator workflows. For IT teams, all activity is logged and encrypted with customer-managed keys, and logs can be integrated with other platforms via API.




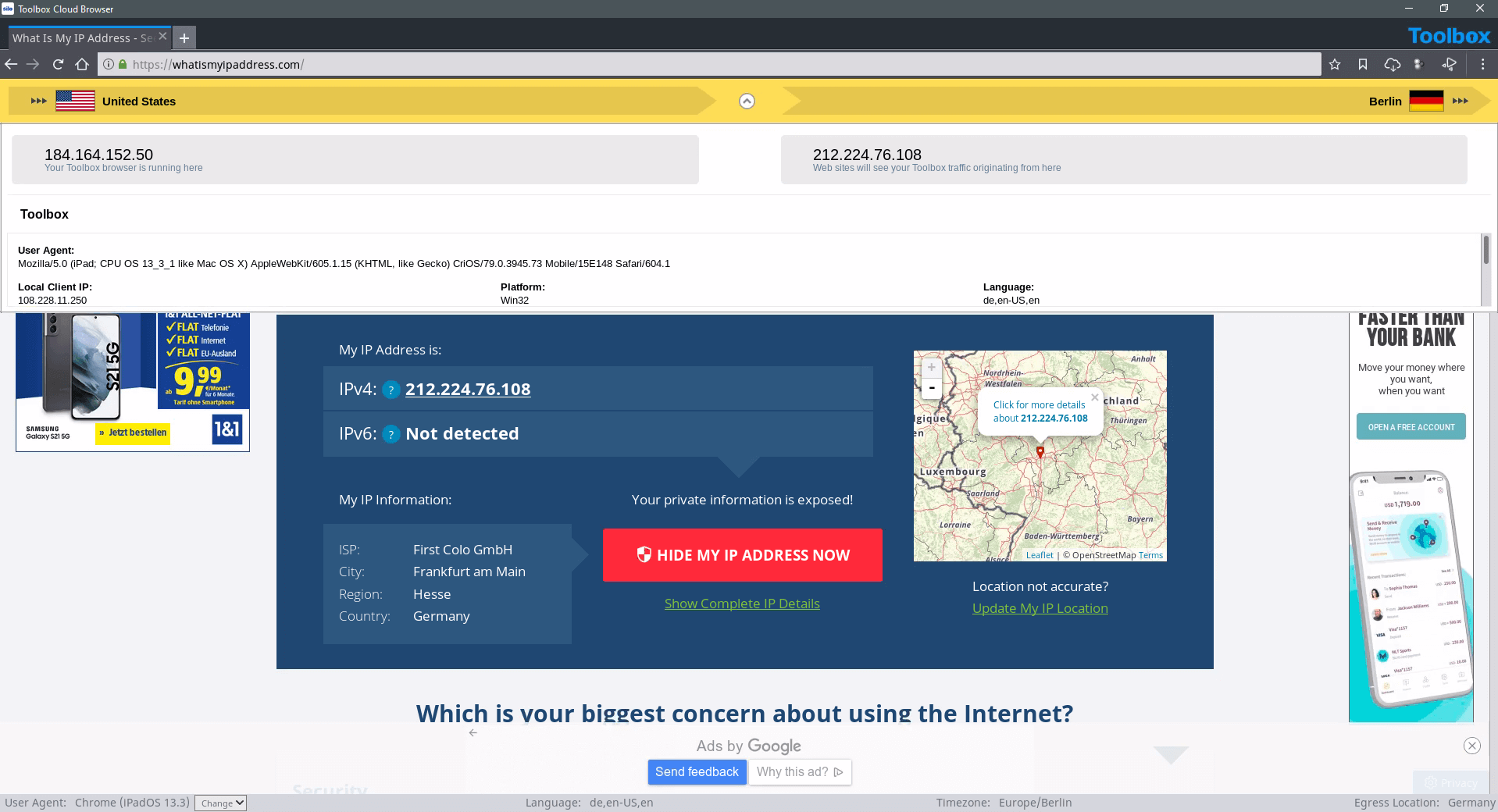
With Silo for Research's managed attribution functionality, you can completely customize how you appear to sites and people you interact with online. Manipulate a variety of your device details including language, time zone and keyboard settings, as well as the browser, OS and other elements. Appear to be browsing from any of Authentic8's dozens of global egress nodes, and show a local IP address that never refers back to you or your organization.
Yes, dark web access is seamlessly integrated within Silo for Research and its suite of analyst tools. You do not need a separate, standalone dark web browser. This integration provides investigators with full isolation from dark web cyberthreats (e.g., malware-laden sites, forums, marketplaces) and anonymity from counter-surveillance efforts utilized by malicious actors.
Yes, Silo for Research integrates with Authentic8 Secure Storage, an encrypted, audited and cloud-based storage repository for users and groups. Investigators may be required to capture and collect content as part of their process. And to maintain efficacy of potential evidence, a proper chain of control and evidentiary requirements must be met.
Collected data needs to be logged, attributed to an analyst and checked for validity. Chain of custody protections are critical to proper collection. When using Silo for Research collection tools — whether manual or automated — all aspects of the process are logged and available for post-facto review.
Yes, Silo for Research is a FedRAMP-authorized service. It has been assessed and approved as a cloud service offering (CSO) that meets the stringent security requirements to process, store and transmit federal government data.