Network security perimeters have changed dramatically in effectiveness in the last several years. Learn how cloud-based web isolation powers an elastic security model where organizations can construct perimeters wherever and whenever they deem fit.
The perimeter is a traditional concept in IT security, but it has become rapidly obsolete as originally defined. The shift to the cloud, remote work, BYOD and reliance on third parties have blown gaping holes in the effectiveness of perimeters of old. As such, these trends have also spurred innovation to achieve the same ends as the traditional perimeter but in a decentralized, digitized, cloud-first world.
Organizations now need a perimeter that can be created anywhere, any time in an instant; expands and contracts as their workforce and attack surface changes; and applies control not just around the network, but wraps protection around specific apps, links and data itself.
The perimeter’s demise and rescue attempts
Back in the day, users, devices, networks, applications and data would all sit locally within the perimeter. Client-server computing meant that trusted users (employees) on managed devices (clients) would access information in corporate applications (servers) and shuttle data back and forth over internal networks. In other words, all parts of the IT stack were under the control of IT security.
But as data moved to cloud apps and users started to work from a variety of locations and devices, the notion of a perimeter as a convenient control point started to crumble.
We live in a more decentralized, cloud-first world, where the attack surface area has become larger, more fractured and harder to reach:
- Data lives in cloud apps
- Users, devices, browsers and networks are varied
- Business interfaces (B2B and B2C) have become web-based
This transition has been underway for many years, with various attempts to stem the tide. For some time, organizations have used VPNs as a weak crutch to trombone user’s workflows through the corporate perimeter to maintain oversight. But this approach has been costly and inefficient — and done in the name of extending the life of legacy tech. What’s more, there are rapidly growing access scenarios where IT cannot mandate end-user software installations (like VPN clients, security agents, extensions and alternative browsers) on connecting devices. Suppliers, contractors, business partners and other third parties that are being granted access to cloud apps are examples of access scenarios that live beyond IT’s control.
As a result, a more elastic and direct-to-cloud security perimeter is called for. But what would this capability look like?
There are four primary attributes that are important in any solution:
Cloud-native flexibility
In a decentralized, cloud-based world, the flexibility to erect a perimeter precisely where and when you need it is crucial.
Solutions that require installation of software on connecting devices and/or users to change their behavior are dead on arrival. A truly cloud-native approach — where users can access web apps natively via their existing browser and are routed through a security service edge — is critical. Not only does this meet the needs of IT when they own the devices, but it addresses the growing scenario where connecting users and devices are not under the organization’s jurisdiction.
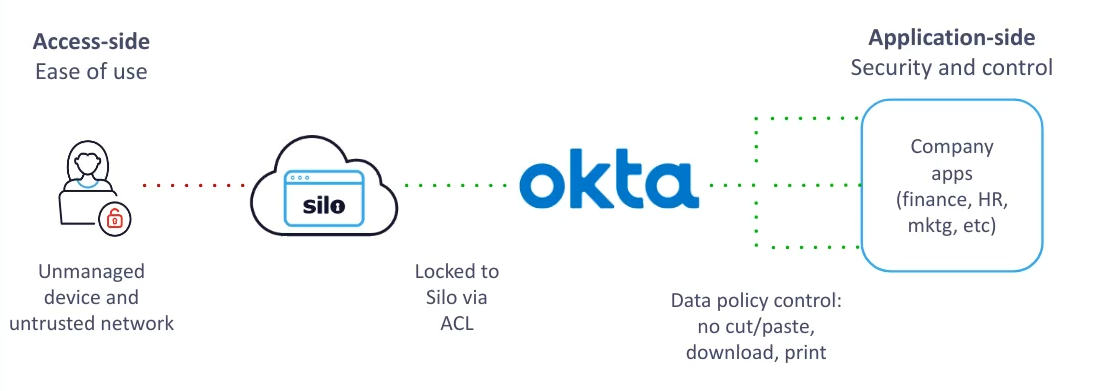
FIG 1 | We recently enabled a cloud marketing platform with secure application access for their 200+ contractors who are using a diverse set of devices, browsers and networks. No software installation or machine configuration was required. By redirecting and enforcing security via an “application-side” delivery model, the customer gained security and control without chasing the long tail of devices on the “access-side” of the equation, over which they have no knowledge or ability to apply controls.
Data isolation
With third parties, BYOD and remote employees, IT is unable to vouch for the integrity of the connecting environment. That’s why applying perimeter capabilities to isolate data and deliver it securely through the “last mile” — regardless of the state of this environment — is so useful.
Secure delivery of data means protection through air gapping against exploits that might be present on the local device, browser or network. Full web isolation is a key capability here to construct a perimeter around applications and their data while allowing ease of access when desired. It ensures that untrusted content and valuable data never come into contact with one another.
Control and visibility
Once users are accessing data in an air gap, it is then important to restrict or allow typical user actions against applications and data as necessary to further manage risk.
Controlling data up/download, printing, copy/paste actions or displaying a web app in a read-only state are all examples of how cloud data can be further ring-fenced when needed. For instance, an employee accessing an app from a personal computer can be granted access in isolation but without the ability to download it locally. But the same employee switching to a managed device might get free reign to access the data without restrictions.
Finally the ability for IT to gain oversight over user activity, especially in arm’s length access situations, is critical in this new perimeter. Administrators should have the ability to observe and audit data access, set specific policies to manage risk, and then edit and revoke them in a centralized place even when they don’t ultimately control connecting users and devices.
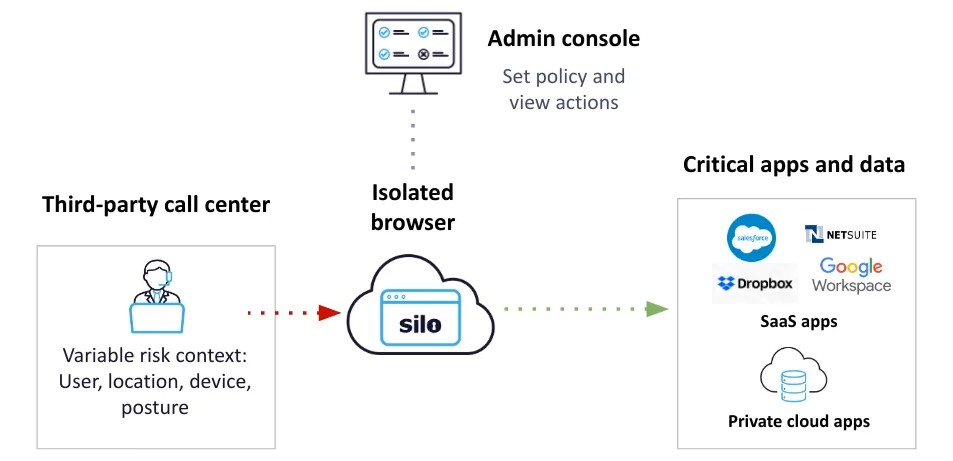
FIG 2 | We have a distributed call-center customer where agents access cloud apps from a secure, air-gapped and policy-enforced workspace. The ability to set central data governance policies around that workplace and audit it globally through a single interface is key.
Context-driven access
A solution that can dynamically adjust access rights based on context is a must-have to meet the realities of today’s access diversity. Organizations have already invested in many tools that can measure and assess risk, and can therefore identify different access permutations:
- User: identity, risk-score, data access rights, typical access patterns, etc.
- Device: identity, location, posture (unpatched, vulnerable, etc.)
- App/data: private vs. public, data classifications, typical access patterns, etc.
Using context to escape the block-or-allow dichotomy
Despite this sea of context, most organizations are still shoe-horned into a binary block/allow decision — which can hurt productivity if screwed too tight, or compromise security if set too loose.
A cloud-native and flexible security model should be able take these inputs and dynamically deliver access rights commensurately. The same user accessing the same app from different environments might warrant air-gapped delivery, with data transfer restrictions in one scenario, but not in another.
Isolated delivery and policy enforcement create a dynamic toolset to deliver a tertiary set of outcomes for security teams to break the block/allow tradeoff.
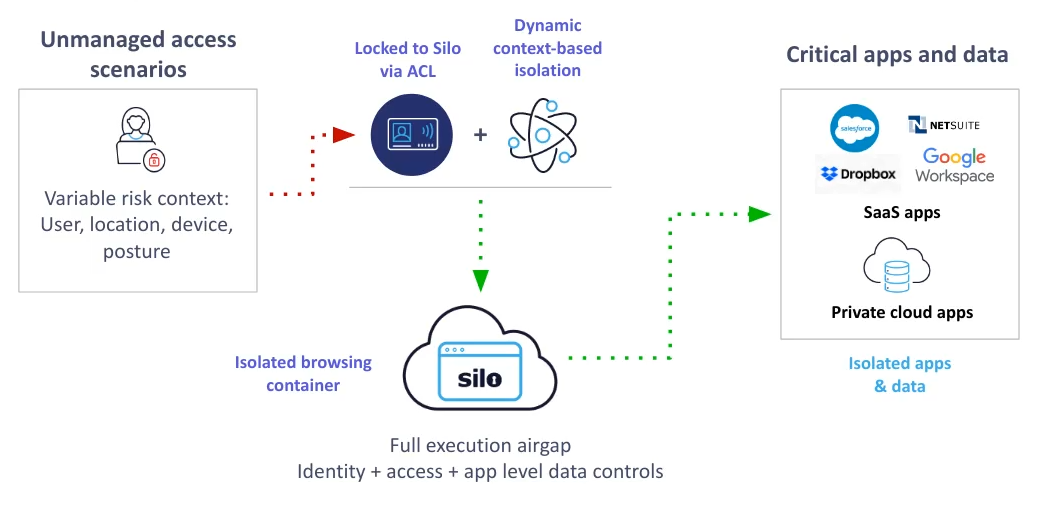
FIG 3 | Our cloud marketing platform customer is able to consider a flexible security model by integrating our secure access platform into their current identity and access management layer (IAM). The IAM brokers authentication of contractors to cloud services, but is also aware of contextual factors such as user’s rights, location and device. By combining these factors and calling our cloud-native isolation platform, they get fine-grained variable control over how they deliver their data.
Cloud-native web isolation as the next-gen perimeter
A configurable and cloud-first web isolation platform like Silo can offer many of these benefits in a way that truly meets the needs of the modern workplace. Viewed through the four attributes described above, the result is an elastic security model where organizations can construct perimeters wherever and whenever they deem fit and provide context-based security to deliver applications and data in even the hardest to reach, but increasingly common access scenarios.
Learn more about how the Silo Web Isolation Platform delivers a flexible, dynamic cloud-native perimeter.
Read why Cato Networks embraced Silo to augment their SASE delivery capabilities.
Tags Secure web access Zero-trust app access

