Intelligence analysts, law enforcement, legal investigators, and investigative journalists all analyze metadata stored with digital images to gather insights about people, events, and locations worldwide. How does it work?
To illustrate a typical workflow for you, Authentic8's Open Source Intelligence (OSINT) team has created a Flash Report based on a real-world example. The overview, titled What is Exif Data?, explains how to distill relevant information from Exchangeable Image File Format (Exif) data.
The document describes how to use specialized tools to extract information about where an image was taken, the camera make and model, and other details. For the Flash Report, our analysts used the FotoForensics app and a photo of a container vessel from a ship-spotting forum.
Image (metadata) analysis has long been a staple of intelligence collection by federal agencies such as the NSA, CIA, DEA, and FBI, as well as numerous other law enforcement, public safety, and digital forensics experts.
More recently, corporate security and protective intelligence professionals, private investigators, investigative journalists, and fact-checking outlets routinely conduct image research and metadata analysis.
Recent examples where Exif data analysis played a crucial role:
And before you ask - yes, Exif data can also be manipulated, replaced, or stripped from digital pictures altogether. Several social media platforms have begun to remove Exif data from images or replace it with their own (tracking) code.
User-uploaded digital camera and smartphone images in online forums, including on the dark web, and blog pictures often still contain Exif data. This makes them go-to sources for Open Source Intelligence (OSINT) researchers and investigators.
What prompted social media services to remove Exif data? There are mainly two reasons. The first is obvious - the second, not so much, but online researchers better be aware of it.
The first reason most social media services give for stripping Exif data from user-uploaded pictures is to protect member privacy and prevent abuse.
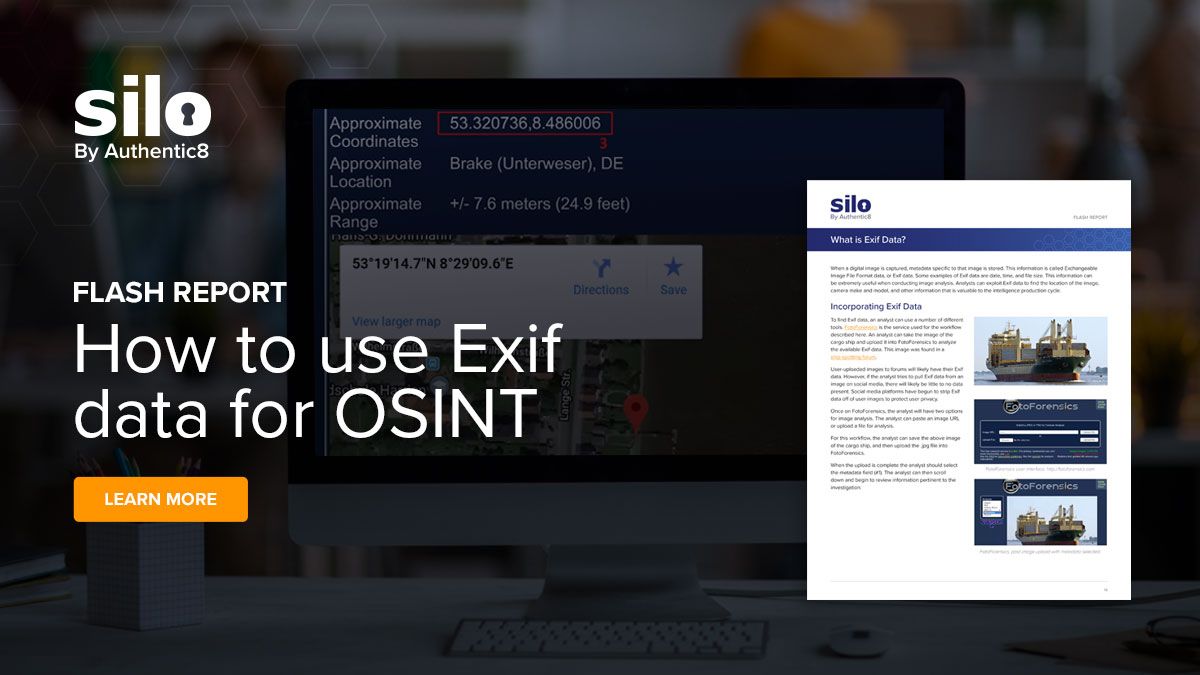
Get the flash report "What is Exif Data?" and learn how to extract and incorporate Exif data into your research here.
Exif data of family photos taken at home, for example, can open the door for doxxing, the publication of private information (such as the residential address) of people against their will, for example of critical journalists, or for cyberstalking.
The second, lesser-known reason is that Exif data can be used to hide malware in image files to launch a multi-stage attack on the device where the picture is viewed.
Security researcher Shyam Sundar Ramaswami recently documented an example found in the wild on the Cisco Umbrella blog. In this case, the exploit code was hidden in the Exif data header of a JPEG image. His warning: "JPG malware is not that common, but it can be very nasty."
Many security professionals and OSINT analysts use Silo for Research (Toolbox) instead of a regular browser when conducting online investigations that involve the collection and analysis of image metadata. They chose Silo for Research for mainly three reasons:
Silo for Research enables researchers to deploy relevant image analysis web apps without risking attribution or exploit should one of these apps be compromised.
The tools at their disposal range from FotoForensics (our Flash Report example) to the Image Verification Assistant, which features image tampering detection algorithms, metadata analysis, GPS Geolocation, EXIF Thumbnail extraction and integration with reverse image search via Google.